McAfee Web Gateway (MWG) is a pretty phenominal product, if you’re looking for a commercial web filtering solution then MWG should certainly be something you should investigate. If however you already have a MWG and are looking at a rule base to make sure that your users can only logon to your approved Microsoft Office 365 domains then read on.
Microsoft Office 365 (O365) is a pretty phenominal product, if you’re looking for a collaboration system then O365 should be something you should investigate. If however you want to make sure that only your organisation can log on to O365 via your network then read on.
Say you’ve invested in Office 365 and your work email address is [email protected] and you don’t want someone to logon on your network as [email protected] this rule set is for you. This method allows you to whitelist domains you want to allow to access services through your MWG and therefore will block personal Hotmail or Live accounts unless you specify these domains accordingly.
In other words you block and control access to Office 365 by blocking domains.
Please note you will need to do at least some HTTPS decryption for this to work, but it does work across Office 365, Azure Applications and things like One Drive. If you’ve whitelisted the O365 ranges you’ll need to fine tune those rules to allow decryption of the login portal at login.microsoftonline.com. Any service which uses the host login.microsoftonline.com will be checked.
Micosoft tell us you own your own data and they make it easy to do so with the likes of strong crypto built in, but they don’t make it easy for us to own our own connectivity. If like many organisations you’ve moved your email onto Office 365 and you’ve whitelisted it through our proxies and firewalls then those not from our organisation can logon already, it makes moving data off a site fairly trivial. With the instructions below you’ll be able to control your own information flows better.
Demo
This is what your users will see when they try and logon. In this demo I’ve used microsoft.com as the allowed domain.
Instructions
If you want to download a ready made XML rule set to import, scroll down in this post…
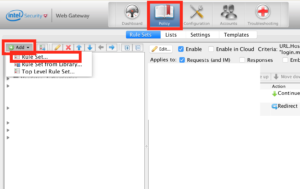
Firstly logon to your MWG as nomal.
Click on “Policy” – “Add” – “Rule Set”
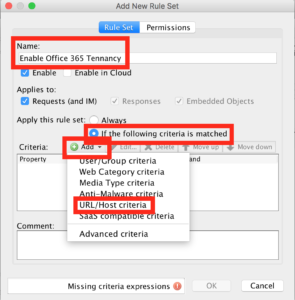
On the box that pops up, give it a sensible name eg “Enable Office 365 Tennancy”, change the “Apply this rule set” to the “URL/Host criteria”.
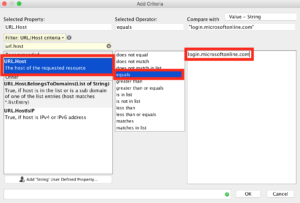
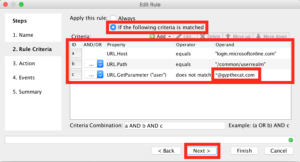
On the next screen that pops up you’ll want to match “URL.Host” with “equals” and “login.microsoftonline.com” just like this.
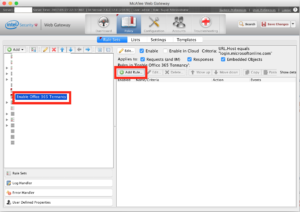
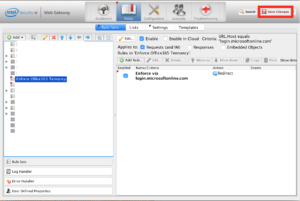
Then back on the main screen, be sure to click on “Add Rule” in the right hand panel.
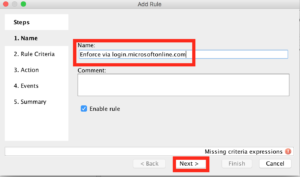
You’ll want to fill these dialogue boxes in like the following (and you can click on the picture for a bigger version):
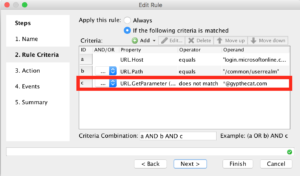
This next one involves quite a lot of clicking and typing, I won’t walk you through each step, but you want the finished version to look like the following. Be sure to change the “*@gypthecat.com” string to your own domain, eg the one you use at current. Click “Next” when you’re done.
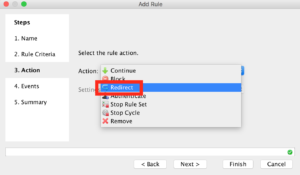
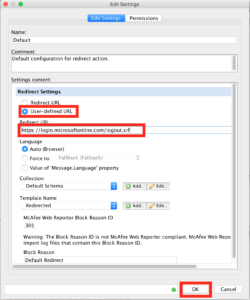
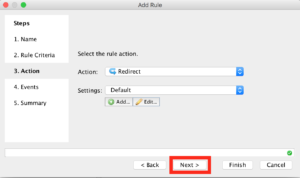
Under Action you’ll want to “Redirect”.
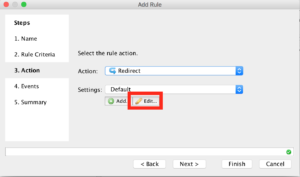
Then click “Edit”.
Populate the box like the following, you’ll want to use “https://login.microsoftonline.com/logout.srf” as the redirected URL. When you’re done click “Ok”.
Then click “Next”.
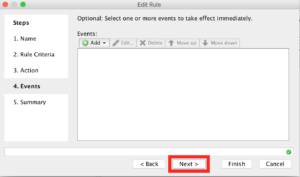
Leave Events blank, and click “Next”.
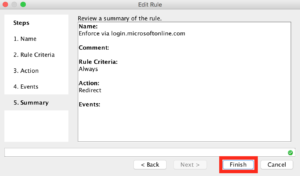
Then click “Finish”.
Back on the main screen, make sure to click “Save Changes”.
Give it a test and it should be good to go!
Troubleshooting
If you’ve been through the above (or downloaded my rule base from below) and you’re having issues have a look at the following;
- If you are whitelisting Office 365 in your MWG policy be sure to have the order of this rule above the whitelist rule.
- You have to be doing HTTPS inspection at least for some sites. If you can access https://login.microsoftonline.com and the certificate doens’t match your MWG CA (ie it reflects a proper Microsoft cert) then you’re not doing enough HTTPS inspection for this to work.
- Microsoft change their O365 domains fairly often, and if they’ve changed the method then you’ll have to do some rule tracing to figure it out.
If you have any other issues feel free to drop a comment below, I will help how I can.
Rule Base Download
If you like please feel free to download the XML file of the rules here:
Enforce-Office365-Tennancy.xml
Uncompress it and import it.
The only thing you’ll need to do is to update the email domain away from “*@gypthecat.com” to the domain of your choice.




No Comment